A sophisticated malware campaign is actively targeting edge devices from Cisco, ASUS, QNAP, and Synology, incorporating them into a botnet known as PolarEdge. This malicious operation has been ongoing since late 2023, leveraging critical security vulnerabilities to execute arbitrary commands on compromised systems.
PolarEdge Botnet Exploiting Cisco Flaw
According to cybersecurity firm Sekoia, threat actors behind this campaign are exploiting CVE-2023-20118 (CVSS score: 6.5), a severe vulnerability affecting Cisco Small Business RV016, RV042, RV042G, RV082, RV320, and RV325 Routers. This flaw enables attackers to execute arbitrary commands, compromising the device’s security.
Due to the end-of-life (EoL) status of these routers, Cisco has not released a patch. However, as a precaution, the company previously advised users to mitigate risks by disabling remote management and blocking ports 443 and 60443.
How PolarEdge Deploys Its Backdoor
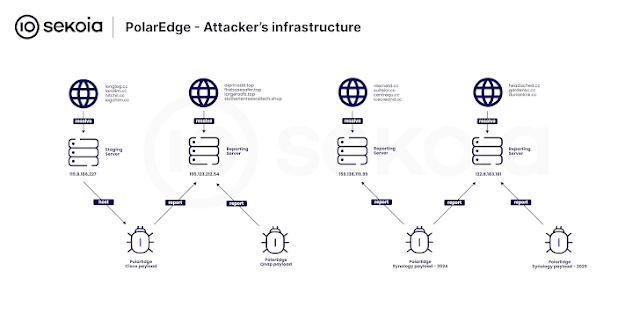
In a recent attack observed through Sekoia’s honeypots, the vulnerability was exploited to deploy a previously undocumented TLS backdoor. This implant is designed to listen for incoming connections and execute attacker-controlled commands.
The infection chain involves:
Deploying a shell script named “q” via FTP post-exploitation.
The script removes log files and terminates suspicious processes.
It downloads a malicious archive t.tar from 119.8.186[.]227.
Extracts and executes a binary called cipher_log.
Establishes persistence by modifying /etc/flash/etc/cipher.sh to repeatedly execute cipher_log.
Once executed, PolarEdge enters an infinite loop, setting up a TLS session and creating a child process to handle client requests and execute commands via exec_command.
Expanding Targets: ASUS, QNAP, and Synology Devices
Further investigation uncovered PolarEdge payloads targeting ASUS, QNAP, and Synology devices. These malicious artifacts were uploaded to VirusTotal by users in Taiwan. The payloads are distributed via FTP using IP 119.8.186[.]227, an address associated with Huawei Cloud.
Currently, 2,017 unique IP addresses have been identified as compromised, with most infections observed in:
United States
Taiwan
Russia
India
Brazil
Australia
Argentina
What is the Objective of the PolarEdge Botnet?
Security experts have yet to determine the precise goal of the PolarEdge botnet. However, researchers speculate that it aims to control infected edge devices, potentially transforming them into Operational Relay Boxes for launching cyberattacks.
Emerging Threat: 130,000-Device Botnet Targeting Microsoft 365
This disclosure coincides with findings from SecurityScorecard, revealing a massive botnet of over 130,000 infected devices conducting large-scale password-spraying attacks on Microsoft 365 (M365) accounts.
This attack exploits non-interactive sign-ins with Basic Authentication, a method commonly used for service-to-service authentication and legacy protocols like POP, IMAP, and SMTP. Since these sign-ins bypass multi-factor authentication (MFA), they create a significant security risk.
Key Insights from SecurityScorecard
The attack infrastructure is linked to Chinese-affiliated groups, including CDS Global Cloud and UCLOUD HK.
Attackers use stolen credentials from infostealer logs to gain unauthorized access to M365 accounts.
Non-interactive sign-in logs are often overlooked by security teams, allowing attackers to conduct high-volume password-spraying attacks undetected.
Protecting Against PolarEdge and Emerging Cyber Threats
Organizations and individuals using Cisco, ASUS, QNAP, and Synology devices should implement the following security measures:
Disable remote management on routers and block access to vulnerable ports.
Apply available firmware updates or upgrade to supported hardware.
Monitor network logs for unusual activity and implement intrusion detection systems (IDS).
Regularly audit device configurations and restrict access based on least privilege principles.
Use strong, unique passwords and enable multi-factor authentication (MFA) wherever possible.
As PolarEdge continues to evolve, its target range and attack methods may expand, posing significant cybersecurity risks. Staying proactive with robust security practices is essential to defending against these sophisticated threats.