The U.S. Federal Bureau of Investigation (FBI) has officially attributed the record-breaking $1.5 billion Bybit hack to North Korean cybercriminals, intensifying concerns over state-sponsored attacks on the cryptocurrency industry. Bybit's CEO, Ben Zhou, has declared "war against Lazarus," vowing to take action against the notorious hacking group.
FBI Links Bybit Heist to TraderTraitor Group
According to the FBI, the Democratic People's Republic of Korea (DPRK) was behind the massive crypto heist, linking the attack to a well-documented threat cluster known as TraderTraitor. This group, also identified as Jade Sleet, Slow Pisces, and UNC4899, has a history of targeting Web3 firms through social engineering tactics and malicious software.
"TraderTraitor actors are rapidly laundering the stolen assets by converting them into Bitcoin and dispersing them across thousands of blockchain addresses," the FBI revealed. "These funds are expected to be further laundered and eventually cashed out into fiat currency."
This isn't the first time the TraderTraitor cluster has been implicated in high-profile crypto thefts. In May 2024, Japanese and U.S. authorities connected the same group to a $308 million attack on DMM Bitcoin.
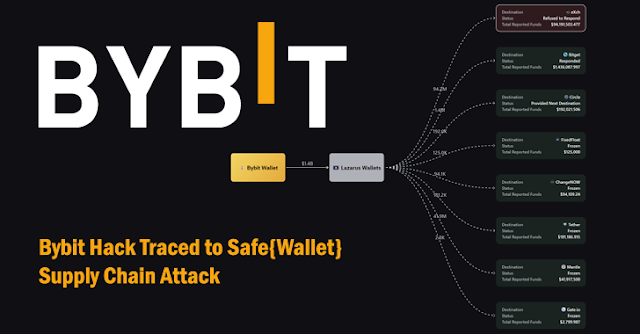
How the Bybit Hack Unfolded
The attack reportedly stemmed from a supply chain compromise of Safe{Wallet}, a popular multisig wallet provider. Investigations by Sygnia and Verichains concluded that the hackers injected malicious code into Safe{Wallet}'s infrastructure, which later compromised Bybit’s Ethereum Multisig Cold Wallet.
Key Findings from the Forensics Investigation:
Verichains' analysis found that the JavaScript file of app.safe.global was replaced with malicious code on February 19, 2025, at 15:29:25 UTC.
The malicious code was triggered during Bybit’s next transaction on February 21, 2025, at 14:13:35 UTC.
Researchers suspect that Safe.Global’s AWS S3 or CloudFront account/API key was compromised, enabling the attack.
Safe{Wallet} has since confirmed that the breach resulted from a developer’s compromised machine, which allowed the attackers to inject a malicious transaction proposal. The company has implemented additional security measures to prevent future incidents.
North Korean Hackers Exploited Fake Job Interviews
A parallel investigation by Silent Push uncovered that the Lazarus Group registered the domain bybit-assessment[.]com at 22:21:57 UTC on February 20, 2025, just hours before the hack occurred.
Key Evidence Linking Lazarus to the Attack:
WHOIS records show the domain was registered using "trevorgreer9312@gmail[.]com," an email linked to Lazarus Group’s Contagious Interview scam.
The Contagious Interview operation lures victims via LinkedIn job offers, tricking them into downloading malware disguised as assessment tools.
This technique enables credential harvesting and unauthorized access to corporate and financial systems.
Bybit’s Response and Industry-Wide Impact
Bybit has launched a bounty program to track and recover the stolen funds. However, the company has criticized eXch for failing to cooperate in freezing the stolen assets.
"The stolen funds have been funneled into untraceable destinations, including exchanges, mixers, and bridges. Many have been converted into stablecoins that can still be frozen," Bybit stated. "We need cooperation from all involved parties to either freeze the assets or track their movement."
Lazarus Group’s Growing Crypto Heists
North Korean hackers have stolen over $6 billion in crypto assets since 2017, fueling the regime's illicit financial operations. The Bybit hack alone surpasses the $1.34 billion stolen across 47 crypto heists in 2024.
The attack underscores the increasing cybersecurity risks in the cryptocurrency industry, highlighting the urgent need for enhanced supply chain security, multisig wallet protections, and industry-wide collaboration to combat cyber threats.